22/02/18 Updated with another one further down the page.
No 1
Having just received this I thought I’d share it. This may be nothing new to you but in case you’ve never seen this…
Company Directors, CEOs and business owners are easy to find on the Internet, as are Finance Directors and other credit control/accounts personnel. We have had many emails sent into us in the past where someone has sent in a message that appears to come from a Director or other key person in the business to one who is responsible for paying the bills.
In this case it was pretty obvious because it was sent from me to our accounts address and I know I didn’t send it. The other thing is that the only people who call me Jeremy and not my nickname Jez are people who have found my real name in company records.
There are other instances where it is even more clever and the email has been sent via a company server and standard disclaimers added. This is one of an exponentially growing number of circulating scams designed to relieve you of your money.
The original message:
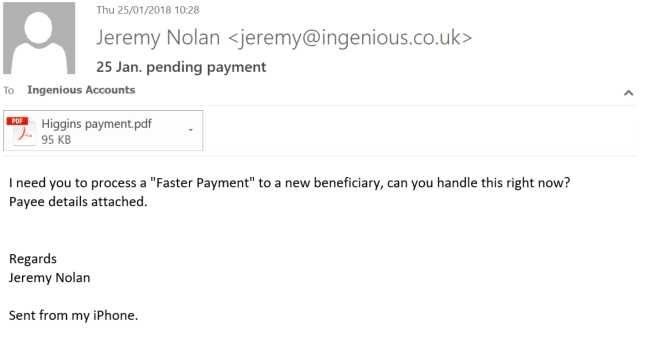
Looks okay doesn’t it? That is, apart from the fact I am not Jeremy Nolan on our systems, have no idea who Higgins is and don’t have an iPhone. Others are far more sneaky and get these facts correct.
So – what do you do? Normally I would have just deleted it immediately but thought I’d illustrate a few things you can do if you think it might be genuine and have already opened it.
The best thing is not to open it and independently verify the message – by phone/text/new email but NEVER reply to this one (see why below). You really must get into the habit of doing on all emails where money or other confidential information is involved.
DO NOT UNDER ANY CIRCUMSTANCES OPEN THE ATTACHMENT.
If you have opened the message there are two things that are an immediate giveaway but both are subtle and one needs a little digging:
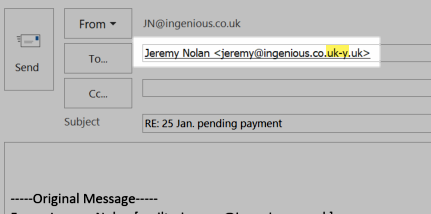
No 1. The reply to address had been changed – and it is easy to miss this:
No 2. You can also find this in the message headers:
Click on the tiny expanding box in the Tags section of the Ribbon in Outlook and then highlight all the text in the Internet Headers box, Ctrl-c to copy…
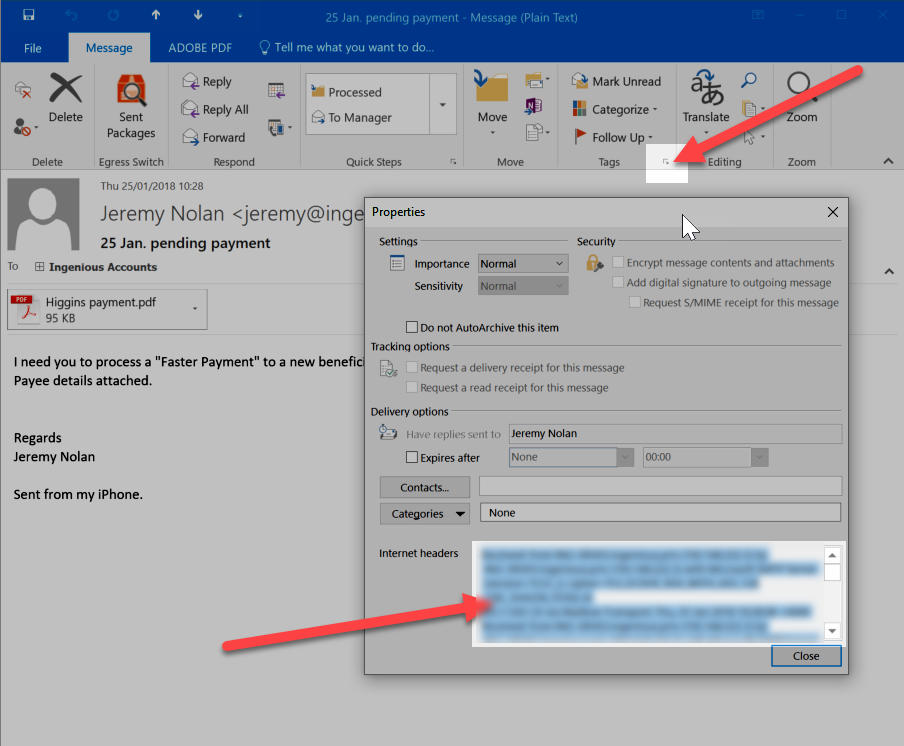
…open Notepad and Ctrl-v to paste in.
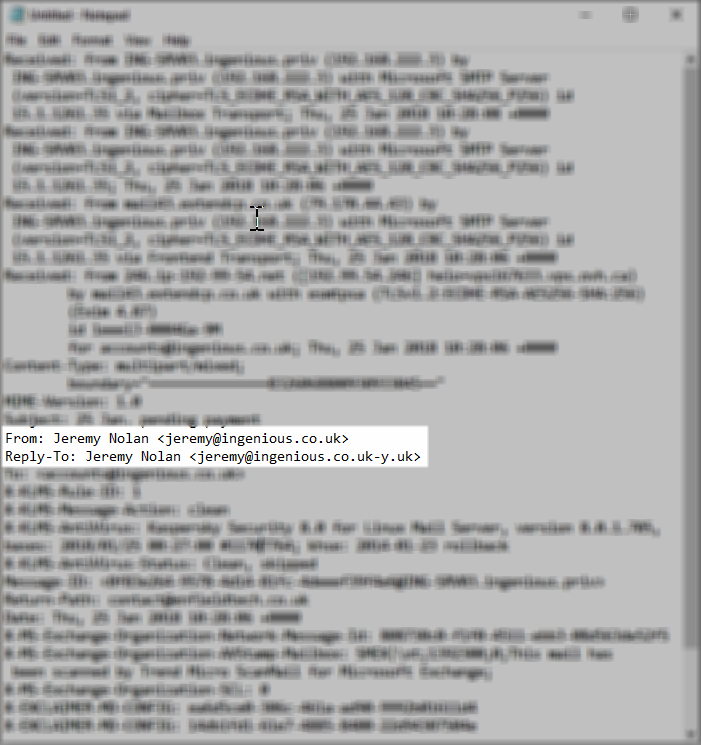
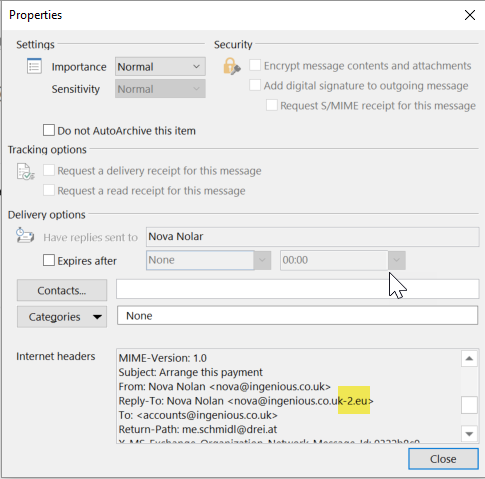
Notice the From address and the Reply-To address are different – the reply to address has been set to a uk-y.uk domain and not ingenious.co.uk.
This is important because any reply to this message will go to an external email account that will almost certainly result in a conversation trying to get you to carry out the transaction.
No 2
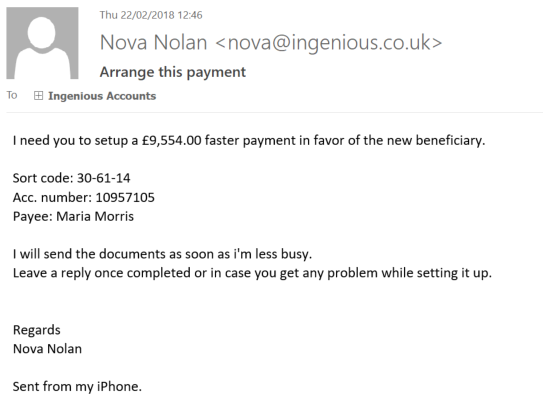
This one is similar to the one above but far more convincing. It looks like it has come from my wife who helps us with the accounts.
There are some minor mistakes – I know her default e-mail address is nn@ and not nova@, she would e-mail me direct rather than our accounts address, she wouldn’t spell favour ‘favor’ plus she would never sign it “Regards, Nova Nolan” to me. It is also rather bad grammar and not her style of writing!
But in essence it all looks fine.
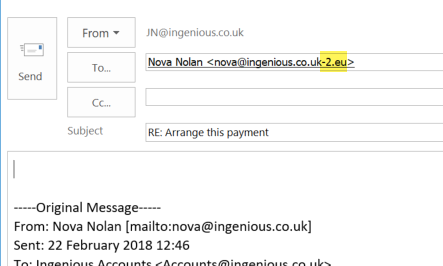
Again if I click on reply the reply to address is not quite right:
And the message headers also give the game away:
The Moral of the Story?
Treat ALL communication as suspicious. Set your default response to not trust it whatsoever and work back from that stance.
Aside from that there are numerous protection mechanisms and best practices we can help you with.
BUT – it is important to know that YOU (and the rest of the people in your organisation) are the easiest target. This sort of trickery is rife and it is not going to stop!

