You should have some IT security already in place. If you outsource your IT support, your service provider will have recommended some basic tools such as anti-virus. The question is – do these address all of the IT security issues that your company faces today? Do they address what can be your biggest security risk?
Your Staff
Your company is only as secure as its weakest link and that weakest link can often be your staff. For various reasons, IT security and best practice training for employees is rarely a priority in business. You may be pressed for time or simply lack the resources to provide adequate training. This is an issue when it comes dealing with security threats. Email trickery and scams – employees should be able to spot suspicious activity, phishing or spoof emails.
Unfortunately, it doesn’t take much IT skill to go phishing and various tools exist on the dark web to enable hackers to pose as legitimate users or institutions. This allows them to retrieve confidential and secure information and is becoming increasingly more common as the barrier to entry is low. It is simply easier than more traditional hacking. Watch the video at the bottom of this page for and example of Vishing – voice phishing as an example of how crafty this can get.
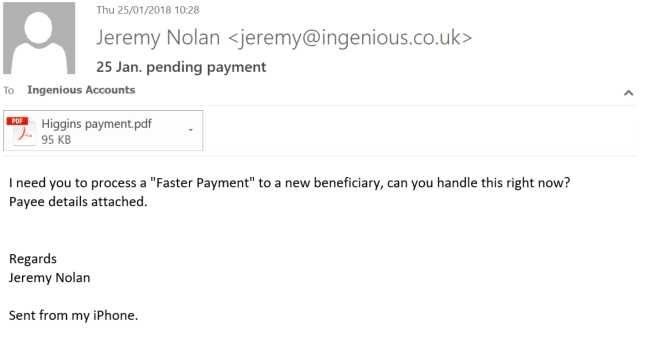
A common example is people posing as legitimate staff and key influencers within your business and asking employees to change payment details or processes, which is when the scam takes place. An alternative name for this is Impersonation, simply because that is what they are doing. Would your team know what to look out for in a situation like this? What, for example, would your staff do if they say an email like the one below and detailed on this page?
IT Practices
User accounts often have unrestricted access to local machines and network resources. Commonly, this was allowed for convenience, but is now a risk that should not be taken. Giving wider access to some users is perfectly acceptable. For the majority, however, things should be as restrictive as possible while allowing them to do their job. This includes not having local administrator rights (required to install applications). Not doing so is a significant security risk you needn’t expose the business to.
Furthermore, working from home with remote access to the office poses similar security concerns. It can be convenient for employees, but is convenience as important as keeping your data and information secure? This, again, needs to be locked down and controlled.
Devices
The practice of ‘bring your own device’ (BYOD) to work is a common issue for IT security. Employees like having their own choice of phones, but who manages these devices? Nothing forces users to password/pin protect their mobiles. What happens if they’re lost or stolen? This is significant, considering the amount of corporate data that resides on them. If employees leave your organisation, whether or not to join a competitor, can you partition and wipe the company data on these devices? BYOD brings with it various IT security concerns.
Passwords
The problem even comes down to the simple IT processes of creating and managing passwords. Typically users will provide the same password across multiple accounts, sometimes with slight variations for each. And they often kept the same password for years. Once one account is compromised, it’s then easy for hackers to access others. Convenience vs security once again – is it more important to have secure passwords, or ones that are easy to remember? I know what I would choose for my business.
Attitudes and Approaches
There often is a lackadaisical approach in getting urgent processes and functions working correctly – often resulting in security disasters for many businesses – and procedures for reporting and following-up breaches in security are rarely sufficiently enforced. Again, making way for a major security breach in businesses. For instance, were you aware that you only have 72 hours to gather all related information and report data breaches to the Information Commissioners Office?
Equally physical access to key systems such as communications and server rooms MUST be under lock and key to prevent unauthorised access and misuse of the room. Companies in particular misuse server rooms as junk storage rooms, making way for physical access problems.
These are some of the potential risks and issues you need to be aware of. If you have concerns or want to know more, visit our webpage for more information regarding IT security services.
What Do We Do:
Ingenious provides helps you to strengthen your IT security. We look at what we believe is your biggest security risk and work from there to make your network secure.
You can find more detailed information on our IT security services can be found here.
Vishing example – skip to 1m20s if you are pushed for time but don’t miss the even more scary last 2 minutes starting at 4mins:

